A properly defined, implemented, and managed IT security architecture requires an underlying network architecture that has been subjected to the same due diligence. Unfortunately, corporations rarely have the luxury of a single network framework. Among other things, they often must absorb new elements as a result of mergers and acquisitions; follow regulatory compliance standards within different geographic regions; and handle changes in direction as new analysts, architects, and executives come on board. Over time, and without regular maintenance, network entropy will undoubtedly increase.
A well-designed network architecture is a defendable architecture, i.e., one that reduces cyber risk. Such an architecture would include comprehensive visibility into network traffic and assets; appropriate enforcement of encryption for data at rest and data in motion; visibility into cloud utilization; and management of identities. Organizations often focus on the security effectiveness and performance of their existing security controls to manage cyber risk; however, while these are important, optimizing network architectures can have a greater—and sometimes more immediate—impact.
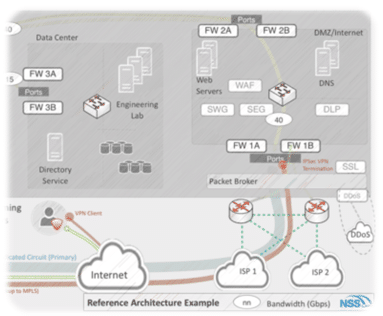
No security control is capable of blocking all threats or mitigating all attacks (the results of NSS’ 2017 Data Center Security Gateway Group Test support this point), but enterprises can use architecture frameworks to improve visibility, reduce response time, and mitigate threats. Additionally, IT security reference architectures (i.e., the type, number, and location of security controls within organizations) provide documentation that can accelerate the implementation of new technologies and help ensure consistent technology use. IT security teams can also use these references to avoid past mistakes.
Some security controls are only as effective as their ability to communicate with each other, which means integration requirements should strongly influence network design. Does the network architecture enable communication between controls (for example, within a breach prevention system) and between controls and cloud access security brokers (CASBs)? For more on interoperability, see our recent blog and paper.
Whether or not an enterprise implements a framework or a reference architecture, it should strive for resilience and adaptability in its network. The architecture must be able to accommodate changes to business and network requirements, and it should be able to recover quickly after an incident or breach. This is possible if the architecture is well designed with regard to product installation location, network routing and segmentation, user access and identity management, and even protocol use.
Frameworks can sometimes add more complexity than they are worth, but where this is true, NSS recommends utilizing more narrowly focused reference architectures with clearly defined success criteria. Often, a security control’s full benefits are not accessed because of architectural limitations rather than because of the product’s limitations. For this reason, time spent evaluating your enterprise network is time well spent.
Jason Pappalexis is managing director of the NSS labs Enterprise Architecture Research Group. He has worked with endpoint protection products for more than 18 years and has held roles in the IT security industry that include administration, architecture, field engineering, and product testing.
NSS Labs recently published results from the 2018 Data Center Intrusion Prevention System Group Test. You can download a free copy of the Security Value Map™ to see how each tested product scored in Security Effectiveness and Total Cost of Ownership.
