Meet Ben, an accountant for a technology startup in Austin. After a great weekend with his pals at Austin City Limits, Ben heads to the office. He logs into his computer and goes through his work emails. Next, he fires up his web browser and navigates to Gmail. He finds an email from LinkedIn entitled “Ben, people are looking at your LinkedIn profile.” Curious to see who’s checking him out, Ben clicks on the link and is sent to what looks like a LinkedIn page; he types in his login credentials and clicks “Sign In.” However, instead of the page presenting his profile after a successful login, it seems that it simply refreshes. Ben tries again and gets the same results. Eventually, he gives up and gets back to work.
What Ben doesn’t know is that he has just infected his computer with malware that allows cybercriminals to steal his corporate banking credentials.
While Ben’s story is fiction, it’s not too far removed from reality. Targeted campaigns are carried out against users of social networking platforms every day, with end goals being much more sinister than just using hacked accounts to peddle clickbait articles. The executive summary of Verizon’s 2017 Data Breach Investigations Report reveals that 73% of breaches were financially motivated, and 43% of breaches included socially engineered attacks.
To combat this challenge, enterprises can deploy secure web gateways (SWGs). These products protect users and applications through features such as policy-based URL filtering and malware scanning. Since the majority of social networking sites and their instant messaging applications utilize HTTP and HTTPS, SWGs can be deployed in full proxy mode, which enables HTTPS traffic to be decrypted, scanned, and re-encrypted. Enterprises that do not filter employee web access make it easy for attackers to deliver malware over common ports (or, as they say, “let them in through the front door”).
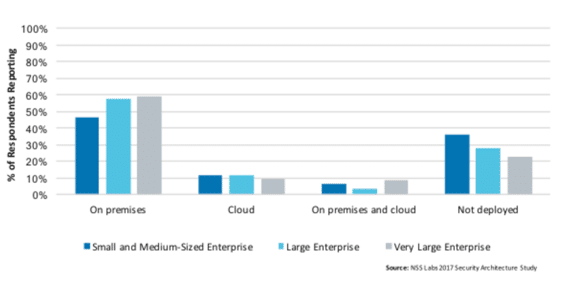
NSS’ 2017 Enterprise Architecture study found that 71.7% of US enterprises deploy SWGs, with over half of these deployments taking place on premises. This study also indicates banking, financial services, health insurance, and insurance industries are strong adopters of this technology. Management of SWG deployments is typically performed by members of security operations teams.
SWGs aren’t the only product enterprises can use when trying to prevent attacks delivered via social networking platforms. Next generation firewalls (NGFWs) incorporate many SWG functions, such as URL filtering, HTTPS inspection, anti-malware, and web application control; however, they often lack web proxy content caching and are less reliable when performing intensive SSL offloading operations. Enterprises seeking a complete solution should consider layering these controls (see our Analyst Brief, Feature Consolidation – What Are the Implications of This Continuing Trend?).
NSS Labs has released a series of Intelligence Briefs that focus on security controls in the US enterprise, one of which is focused on secure web gateway products. The series will report on security product usage as reported by 510 information security professionals representing 50 US industries.
