Rarely do we turn on the TV or read the news without learning of a new cybersecurity breach. Anyone following this news will likely be familiar with the rapid rise of ransomware as well as the record profits its developers are gaining through paid ransom demands. However, what many of these news stories neglect to tell you about is the much larger cost of ransomware to businesses in the way of downtime, lost productivity, and other expenses. For example, the ransomware payments for WannaCry were estimated at a few hundred thousand dollars at most; however, the total cost in damages was an estimated US$1 billion. This year, the total cost in damages due to ransomware is predicted to hit US$5 billion (CSO Online, 2017).
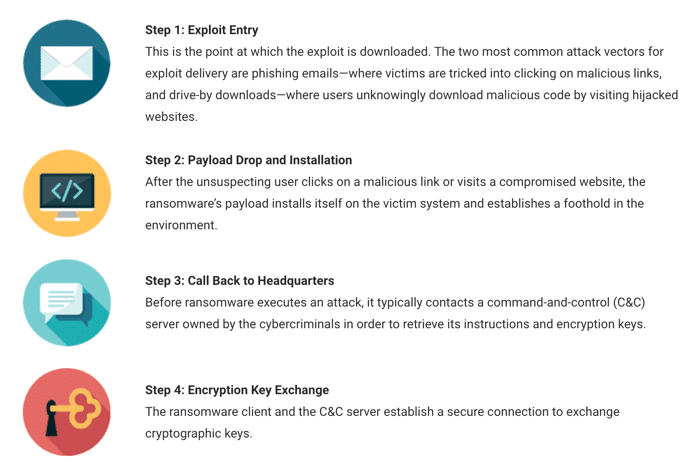
Ransomware attacks are becoming something that businesses can no longer afford to ignore. To protect against ransomware, it is important to first understand how it operates. Although there are a few exceptions, these are the typical steps in a ransomware attack, as outlined in our white paper on Ransomware and the Limits of Conventional Protection:
The bad news is that there is no silver bullet to eliminate the possibility of ransomware targeting your company; however, there are measures you can take to lower the chance that it will succeed in its mission:
-
- Patch management: Out-of-date software is always a risk. Organizations must keep up with patching the security holes in their applications and operating systems to remove vulnerabilities, especially for commonly exploited applications, such as Flash and Java.
- Email scanning: Scan inbound emails for known threats and to block potentially dangerous attachments.
- Advanced endpoint security: Implement and maintain an advanced endpoint protection solution that is capable of detecting both known and unknown malware.
- Web filtering: Use web/URL filtering to control which sites users can access.
- Outbound traffic monitoring: Use outbound traffic filtering to block connections indicative of C&C communication.
- User education: Attacks often succeed because an ill-informed user clicked on a link in an email or opened an infected attachment, which is what cybercriminals are counting on. This is why educating users about security risks is an important first line of defense.
So, what can you do if your company has fallen victim to a ransomware attack? Your first step should be to activate your business continuity plan, identifying which processes are critical to business operations and migrating any affected by the breach to the alternative methods or resources documented in your plan.
You should also report the incident to the proper law enforcement agencies; the FBI Internet Crime Complaint Center (IC3) accepts online Internet crime complaints. In the meantime, your organization should be working to recover the systems and data that were locked or encrypted by ransomware. Decryption keys for some of the older or more common ransomware types are available online, so it may be worth your time to perform a search. If you need a little more time to recover and validate files from backup, some businesses have successfully negotiated a time extension with their attackers through the live chat function built into many modern ransomware interfaces.
The earlier in the kill chain you can disrupt a cyberattack, the better. And with ransomware in particular, it’s imperative that organizations shift their focus to the exploit phase of an attack and proactively validate their security defenses’ effectiveness against known variants of ransomware.
