Breach detection systems (BDS) are physical devices, virtual appliances, cloud services, or managed services that utilize both static analysis and behavioral analysis techniques to detect advanced malware, zero-day attacks, and targeted attacks that have bypassed a network’s existing security controls. Sandboxes were initially developed to scan files for malicious content that may have been missed by existing, signature-based antivirus security controls, and as and an answer to the rise in zero-day targeted attacks.
Since their development, BDS have undergone an extensive evolution. For example, instead of being strictly hardware appliances, BDS are now also available as virtual appliances and cloud-based services. Additionally, deployment has transitioned from out-of-band network deployment (using TAP or SPAN) to include integration with other security controls—next generation intrusion prevention systems (NGIPS), next generation firewalls (NGFW), secure email gateways (SEG), secure web gateways (SWG), and even endpoint products. Today’s sandboxes have become another layer in the traditional security stack—more of a feature than a product—and are even being sold as SKU add-ons by several network security vendors.
Enter the security information and event management (SIEM) product. SIEM products are centralized reporting platforms that bridge business data and security event data, with the goal of making it easier for security teams to understand the relationships between recorded events and authorized/unauthorized activities. Note that a SIEM product is not a security product, but rather it is a tool that acts as a consolidation point for log data, threat information, and business information.
Organizations understand the value of a local malware research team that’s “plugged in” and ready to analyze an unknown file 24/7/365. Additionally, different teams have different uses for a BDS and thus will have differing opinions on its value. For example, an incident response team might require the BDS to provide visibility into the indicators of compromise for a targeted attack on an executive’s laptop, while a network operations team performing periodic firewall tuning might look to a BDS for more general threat information.
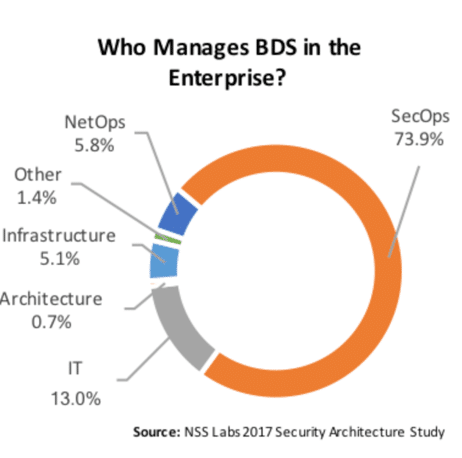
BDS ownership within an organization is divided primarily between security operations (73.9%), IT (13.0%), and network operations (5.8%) teams. It’s not a question of if a sandbox is useful, but rather where it should be deployed, and whether or not the organization has a mature incident response team that can use the information it provides.
NSS Labs is looking forward to continuing our evaluation of security products and helping enterprise security teams understand which products will best fit their environments. This information, along with some unfiltered enterprise feedback, can be found in our Intelligence Brief on Breach Detection Systems in the US Enterprise, which was recently published in the NSS Labs research library.
NSS Labs will be releasing a series of Intelligence Briefs that focus on security controls in the US enterprise, one of which is focused on breach detection systems. The series will report on security product usage as reported by 510 information security professionals representing 50 US industries.
