The 25 (SMTP), 80 (HTTP), and 443 (HTTPS) ports are widely utilized and form the core of business communication. By design, these ports are open across perimeter firewalls. However, this clear line of sight from the dark alleys of the external world to the safe haven of internal users and systems makes these ports especially dangerous.
SMTP port 25 (email) is particularly interesting. The SMTP protocol is relatively simple to use and is easily understood by many, which makes it cost-effective for spammers to send email in bulk. Everyone has an email address, and security headline news in the summer of 2017 seemed to revolve around the high number of phishing attacks and ransomware delivered via email—usually as a URL embedded within an email’s body or within an attachment. Noteworthy breaches using this approach include those of health insurer Anthem, Inc. (2015) and of the Democratic National Committee (2016). It’s clear that this threat vector is not likely to be going away soon.
Secure email gateway (SEG) products are designed to combat these threats through the scanning of inbound and outbound email. I began my security career as an email system administrator for the US government and then covered email gateways as a technical marketing engineer in the early 2000s. Back then, SEG products were in their infancy, but their features were actively expanding (as was enterprise adoption of these products). At that time, SEGs were predominately deployed on premises, placed in line with existing mail transfer agents (MTAs) as physical appliances—or even as virtual appliances—at the network perimeter. Deployment options have evolved, and today cloud-based SEGs are commonplace. SEGs deployed this way provide email pre-filtering that blocks most spam and threats before they hit the on-premises network perimeter and internal mail servers.
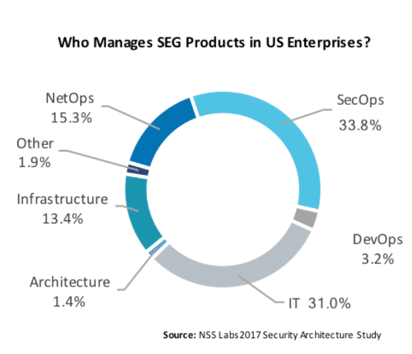
All SEGs require some degree of management. Users must adjust spam thresholds, configure routes and domains, build and modify policies, integrate directory services, and more; multiple teams may share these responsibilities. In a recent study by NSS Labs, it was discovered that SEGs are managed primarily by security operations teams (33.8%), followed by IT teams (31.0%) and network operations (NetOps) teams (15.3%). However, it is rare that a single team owns the entire network stack required to deploy the SEG, and many teams must work together to facilitate deployment.
Email is a perfect vehicle for both legitimate communication as well as cyberattacks, and security controls dedicated to detecting these threats remain crucial.
NSS Labs is releasing a series of Intelligence Briefs that focus on security controls in the US enterprise, one of which is focused on secure email gateways. The series will report on security product usage as reported by 510 information security professionals representing 50 US industries. This paper is available in our research library.
