The volume of log and alert data from just a small number of security products can easily overwhelm a security team—even a well-funded one. “Alert fatigue” is real, and so data consolidation is helpful, not only for timely content consumption, but also to determine relationships between seemingly separate events.
Enter the security information and event management (SIEM) product. SIEM products are centralized reporting platforms that bridge business data and security event data, with the goal of making it easier for security teams to understand the relationships between recorded events and authorized/unauthorized activities. Note that a SIEM product is not a security product, but rather it is a tool that acts as a consolidation point for log data, threat information, and business information.
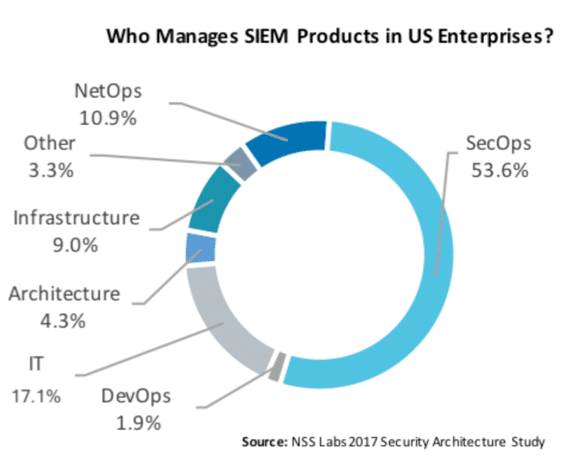
SIEM products are prevalent within security architectures in the US—87.3% of all enterprises deploy one. Due to the tool’s security focus, it is not surprising that SIEM products are primarily managed by security operations teams (53.6%), followed by IT and network operations teams (17.1% and 10.9%, respectively). Regardless of management, multiple teams within an organization must work together to gather the necessary data and orchestrate the installation, management, and tuning of the product, which is no small undertaking.
Unfortunately, once it is deployed, a SIEM product is not a “set-and-forget” type of product; tuning is required to ensure its output aligns with the environment’s needs. And even a tuned SIEM product may not be able to gather the various data and draw worthwhile comparisons within some organizations’ threat detection workflows. One of NSS’ clients expressed the need for an even higher level of logic built into these tools (for example, complex if-then scenarios and user profiles). This next evolution of the product could allow it to act as an architectural monitoring and integrity tool that would enable real-time incident response and forensics.
So, does a SIEM reduce alert fatigue, or does it compound it? Unsurprisingly, SIEM technology has its critics—common complaints focus on complexity of deployment, complexity of tuning, report applicability, and cost. Additional information regarding SIEM deployments in US enterprises can be found in our Intelligence Brief on SIEM in the US enterprise, which was recently published in the NSS research library.
NSS Labs is releasing a series of Intelligence Briefs that focus on security controls in the US enterprise, one of which is focused on security information and event management (SIEM). The series will report on security product usage as reported by 510 information security professionals representing 50 US industries. This paper is available in our research library.
